SSRF/XSPA in MailChimp

Hey!
It's been a while since I blogged about security bugs here, so let me start off once again.
About two weeks ago I found an OAuth based bug that affected Facebook, which since then got patched by their security team and I got some reward for that. This OAuth bug relied on an endpoint which was connected to MailChimp. So I was testing the OAuth2 implementation on MailChimp as the endpoint used by Facebook was connected to MailChimp, while fiddling around with redirect_uri input area provided by MailChimp I found that the web application tried to connect with the URL provided in redirect_uri. So this was something interesting based on the observations below I was able to confirm that the web application was vulnerable to SSRF/XSPA.
Relying on the scheme http://domain:port I was able to port scan Internet facing servers (eg. scanme.nmap.org) for open/closed ports.
So here's the responses I got:
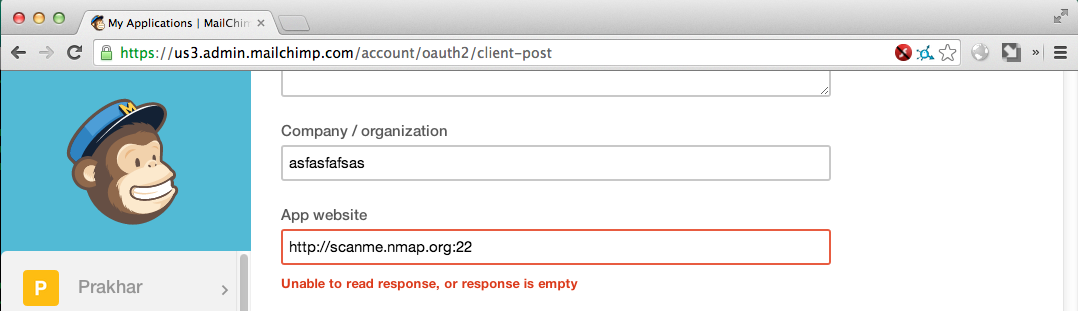
Open Port (running non-HTTP aware service)
Response: Unable to read response, or response is empty
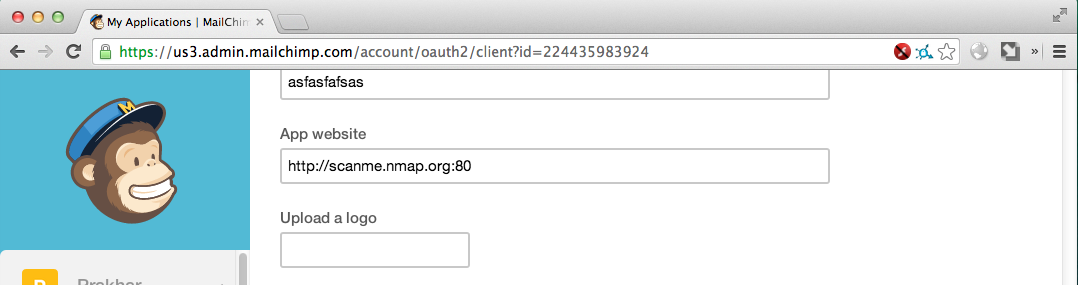
Open Port (running HTTP aware service)
Response: No response/error
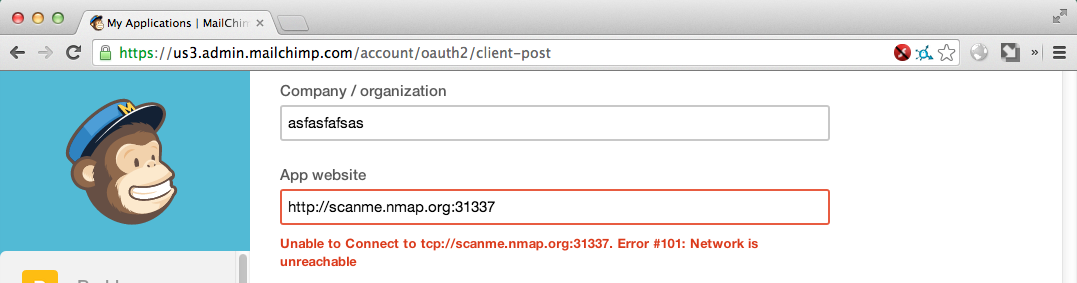
Closed Port
Response: Unable to Connect to tcp://domain:port. Error #101: Network is unreachable
So observing the above request/response pairs we can conduct port scans and automate everything in a scripting language like Python to build port scanners.
MailChimp has confirmed this issue and pushed a fix for this, I was placed in their "Security Response - Thank You" list.