PayPal CSRF aids in account takeover!

A few weeks ago, I found a critical cross-site request forgery vulnerability that forces a user’s primary phone number linked with his PayPal account being changed by hacker’s choice. Before proceeding to discuss on the issue I’d like to introduce you to CSRF verbatim (according to Wikipedia):
Cross-site request forgery (CSRF) is a type of malicious exploit of a website whereby unauthorized commands are transmitted from a user that the website trusts.Unlike cross-site scripting (XSS), which exploits the trust a user has for a particular site, CSRF exploits the trust that a site has in a user’s browser.
Now let’s jump to the vulnerability details, PayPal has a webpage that allows anyone to verify their phone number by sending a confirmation code.
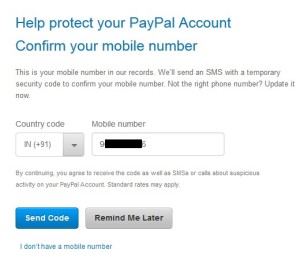
When a phone number is added to the text box and “Send Code” is hit, a POST request is sent to PayPal’s server with phone number, then account’s phone number gets changed with the one specified in the text box.The problem exists when POST is sent to the server, there is no check performed on authenticity of request. So to exploit this scenario an attacker would have setup a webpage, containing code to send a legitimately looking POST request to PayPal server when the page is viewed by the victim which is logged into his PayPal, his account phone number would change.
After all these happened the attacker can easily reset the password, with a requirement that he knows secret questions of victim or his bank account number linked to PayPal. Attacker would initiate a password reset request for the PayPal ID and then select the method of Ownership by Phone.
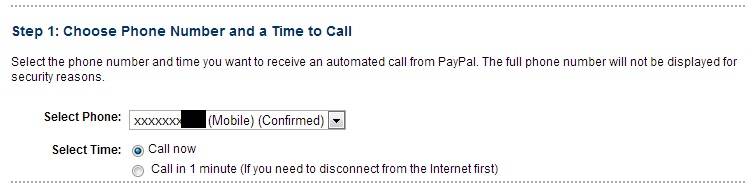
Automated call will be made to the “newly” added phone number from PayPal asking for code that would be displayed on Forget Password Screen after the call has been initiated from PayPal’s system.Once the attacker press the numbers displayed on webpage on the phone keypad when asked, he can proceed to the next step of resetting the password.
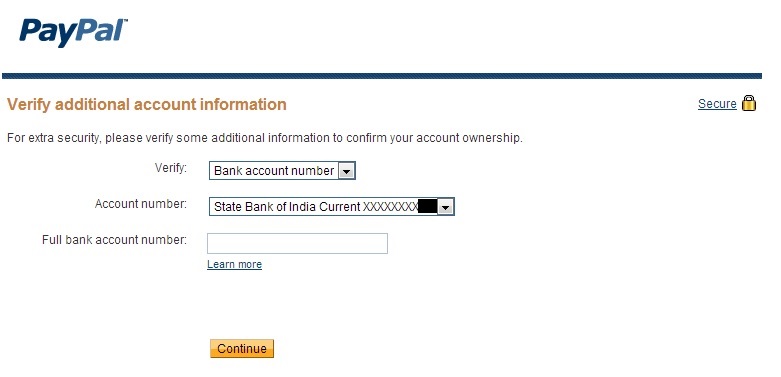
Then attacker needs to answer security questions or bank account number and then he can reset the password.That’s it!
This issue was reported to PayPal as a part of its Bug Bounty program and has been fixed with a reward.