HackerOne Vulnerability: Leaking Common Response Titles

In this blog post I'll explain about the bug I found yesterday at HackerOne which netted me their highest bounty so far (as on 15th Oct 2014 GMT +5:30). The bug was on program/team side which involved common responses of other teams being leaked out through a newly introduced feature called triggers. I'll go ahead and explain every thing in depth.
Common responses are sort of templates for teams, so that they can respond with generic replies for incoming bugs. The URL for each common response have the following format:
https://hackerone.com/common_responses/1234/edit

That's brief information about common responses.Let's talk about Triggers.
Triggers are basically auto-responding mechanism for incoming bug reports, it works by matching certain strings/patterns in incoming bug report. For example let's say if the title of an incoming bug report match the words - Weak Cipher then we can throw a common response automatically and also set an appropriate report state, say - Needs more information. The interface to add a new trigger looks like:
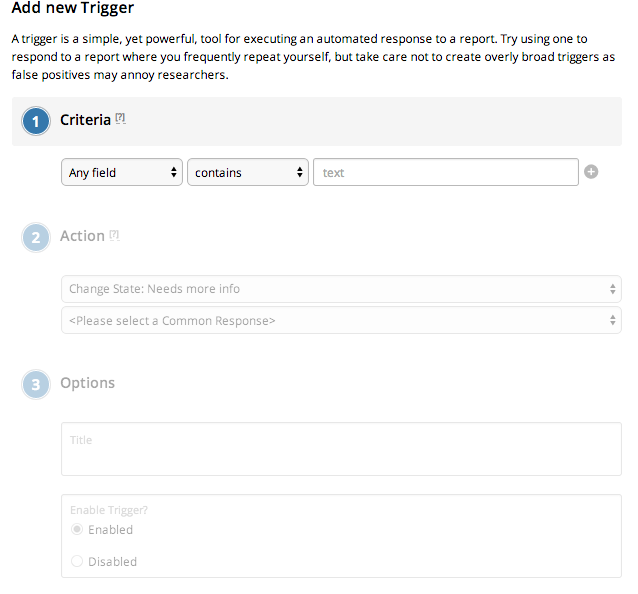
Now, once the details are filled in the form and a common response/state is selected , we can go ahead and activate the trigger. After the trigger activates it looks like the following in the team dashboard.
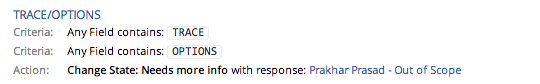
We can see in Action attribute that title of the selected common response is visible clearly. So now let's come to actual vulnerability, which is fairly simple.
While saving a newly added/created trigger, the following JSON is sent to the server:
{
"title": "hackerone",
"criteria": [
{
"field": "any",
"type": "inclusion",
"inverse": false,
"data": "agfagasga"
}
],
"actions": [
{
"type": "request-needs-more-info",
"common_response_id": 24
}
],
"disabled": false
}
common_response_id takes a numeric parameter and sets the appropriate trigger title after the request is passed on to the server and trigger gets saved to the dashboard. As I explained earlier the common response URLs have numeric values, I repeated the HTTP request and modified common_response_id from numeric value 1 to 100 iteratively, and the results were sort of shocking, when each trigger got saved to the dashboard the common responses title of other teams were visible in Action attribute of saved Trigger.
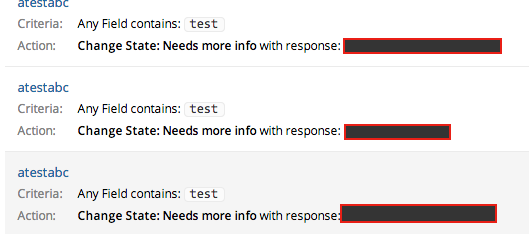
Although I've redacted the leaked titles due to sake of privacy but I can assure you that I'm not trolling and they were really of other teams at HackerOne. So that's all.
I was really very happy to see HackerOne team quickly triaging & patching this bug.They triaged my bug in just six minutes after I hit send report on my side.
Feedbacks are welcome!
- UPDATE: A bug by Daniel LeCheminant netted $5,000 breaking my highest of 2014.