Part V: Exploration - Intruder Payload Processing

Parts of Series
- Introduction to Burp Extender
- Setting Up Extension Development Tools
- Extension Project Structure and Fundamentals
- Diving deeper into Extender API Interfaces
- Exploration - Intruder Payload Processing
In the post, we'll utilise IIntruderPayloadProcessor as a way to explore different Extender API interfaces. By the end of this, we'll have an extension which will perform base64 encode on the Intruder payload set.
IIntruderPayloadProcessor interface contains two method signatures of the following structure, these will be overridden in the implementer class:
-
String getProcessorName(): This will be provide name of the payload processor in the Burp Suite UI. -
byte[] processPayload(byte[] currentPayload, byte[] originalPayload, byte[] baseValue): This is the responsible function for payload processing, the processed payload should return as byte array. We can utilise helpers to convertStringtobyte[]by invokingstringToBytes(); to achieve the oppositebytestoString()can be used.
package burp;
class IntruderProcess implements IIntruderPayloadProcessor
{
IBurpExtenderCallbacks extenderCallbacks;
IExtensionHelpers extenderHelpers;
String processorName = "Base64 Custom Processor ";
public IntruderProcess(IBurpExtenderCallbacks callbacks) {
extenderCallbacks = callbacks;
extenderHelpers = callbacks.getHelpers();
}
@Override
public String getProcessorName() {
return processorName;
}
@Override
public byte[] processPayload(byte[] currentPayload, byte[] originalPayload, byte[] baseValue) {
// currentPayload contains the payload from the list, base64 encode it
String processedPayloadStr = extenderHelpers.base64Encode(currentPayload);
// convert back to byte array and return;
if(currentPayload!= null) return extenderHelpers.stringToBytes(processedPayloadStr);
return currentPayload;
}
}
public class BurpExtender implements IBurpExtender {
@Override
public void registerExtenderCallbacks(IBurpExtenderCallbacks callbacks) {
callbacks.setExtensionName("Prakhar Prasad - Intruder Processor");
callbacks.registerIntruderPayloadProcessor(new IntruderProcess(callbacks));
}
}
The above code is similar to the previous one involving the IHTTPListener interface. We implement IIntruderPayloadProcessor interface in IntruderProcess class and override the methods. Inside getProcessorName() we return the name of the processor payload string which will be visible to Burp Suite's UI when choosing the Invoke Burp Extension (Payload Processing) from Intruder tab.
In processPayload(), when this method is invoked by Burp Suite, we'll receive the current payload (from the list of payloads) in the currentPayload byte array. More information on the other parameters can be found in the Burp Suite API documentation. We do base64 encoding on operation on currentPayload and return the processed base64 payload, which will then be substituted by Burp Suite during the Intruder Attack run.
Steps to Run the Extension:
- Send a sample request to Intruder and highlight the position.
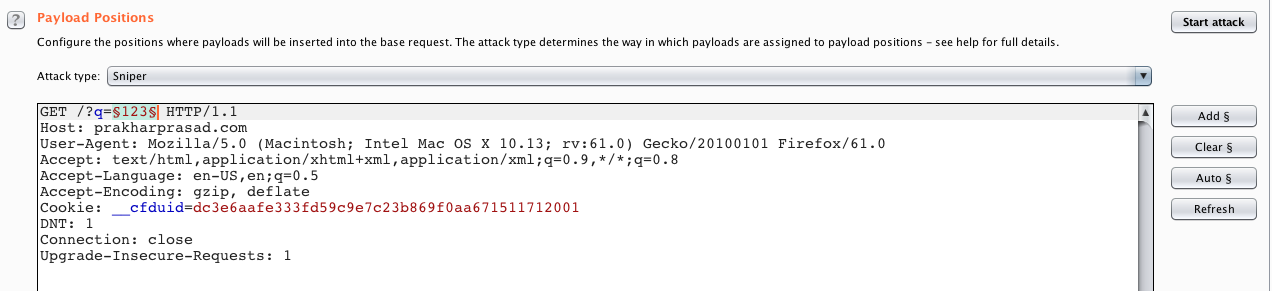
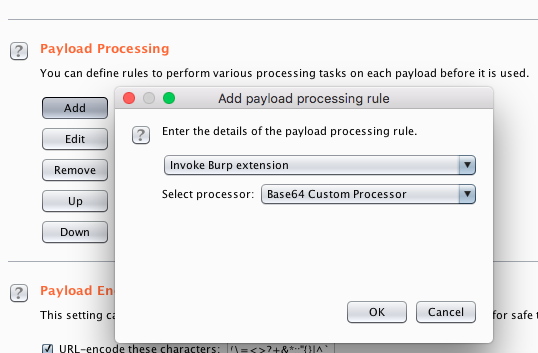
- Select the payload processing and choose Invoke Burp extension and then Base64 Custom Processor [the name which we provided in
getProcessorName()]
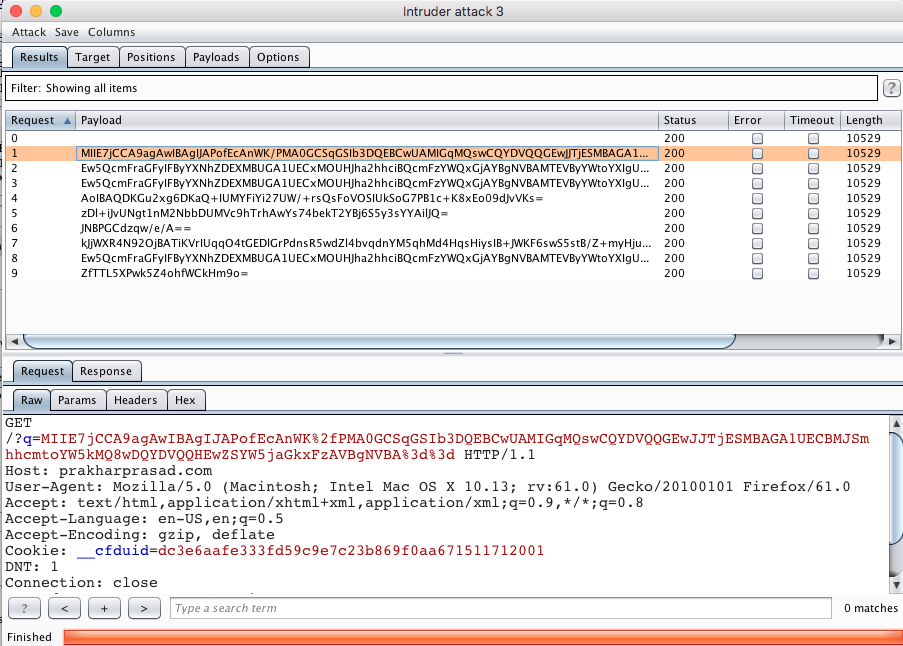
- Select any payload set & type and launch the Intruder attack, you should see something similar to this :
Exercise #3: Write two custom intruder processors to compute the following of the payload set string -
- ROT13
- Reverse the payload string.